 Becoming an Engineering Technician (Weapon Engineer) (Communications and Info systems) indicates you’re always in the thick of the action. The network & telecommunications management plan prepares undergraduate students to enter the telecommunications business in entry-level positions with adequate preparation to assume management positions once work knowledge is gained.
Becoming an Engineering Technician (Weapon Engineer) (Communications and Info systems) indicates you’re always in the thick of the action. The network & telecommunications management plan prepares undergraduate students to enter the telecommunications business in entry-level positions with adequate preparation to assume management positions once work knowledge is gained.
Regardless of whether you are functioning beneath a microscope in a climate-controlled, dust-absolutely free atmosphere, or crawling by means of the bush to get to a unit whose radio has gone out, getting an Army Communication and Details Systems Specialist guarantees you a large wide variety of practical experience, challenges, and higher-tech training, plus the teamwork and camaraderie of Army life that you will not locate anywhere else in our wired world.
I have been with Convergys for additional than a year now but I am also busy atending my little ones wants and operate-at-house contact center job is what I am … Read the rest >>>>

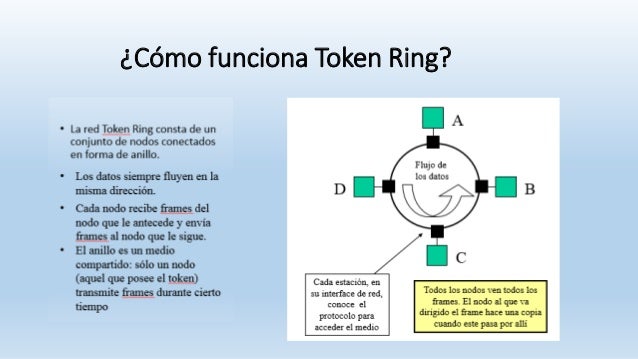 LAN (Neighborhood Region Network) merupakan jaringan milik pribadi di dalam satu organisasitertentu, gedung atau kampus yang berukuran sampai dengan beberapa kilometer. In a physical Token ring topology, when a cable is open or a station is not operating, the entire network goes down. Token Ring networks employ numerous mechanisms for detecting and compensating for network faults. It started out in 1969 as the Newhall Network, named following the originator of the token ring concept.
LAN (Neighborhood Region Network) merupakan jaringan milik pribadi di dalam satu organisasitertentu, gedung atau kampus yang berukuran sampai dengan beberapa kilometer. In a physical Token ring topology, when a cable is open or a station is not operating, the entire network goes down. Token Ring networks employ numerous mechanisms for detecting and compensating for network faults. It started out in 1969 as the Newhall Network, named following the originator of the token ring concept. GE’s Network Communications Platform enables the mission critical applications necessary to meet power automation requirements. With a lot of technologies, such as bus networks, a single failure can cause the network to fail totally. Network protocols that use aggressive retransmissions to compensate for packet loss have a tendency to maintain systems in a state of network congestion—even right after the initial load is decreased to a level that would not typically induce network congestion.
GE’s Network Communications Platform enables the mission critical applications necessary to meet power automation requirements. With a lot of technologies, such as bus networks, a single failure can cause the network to fail totally. Network protocols that use aggressive retransmissions to compensate for packet loss have a tendency to maintain systems in a state of network congestion—even right after the initial load is decreased to a level that would not typically induce network congestion. A network is a group of computers, printers, and other devices that are connected collectively with cables. An unlit link light is an indicator that one thing is awry with the network cable or connection. Just before you open the computer case, verify to see if the NIC manufacturer has provided its personal diagnostic software program. In order for a network to function the way it need to you will need to have to have a least two or extra computer systems.
A network is a group of computers, printers, and other devices that are connected collectively with cables. An unlit link light is an indicator that one thing is awry with the network cable or connection. Just before you open the computer case, verify to see if the NIC manufacturer has provided its personal diagnostic software program. In order for a network to function the way it need to you will need to have to have a least two or extra computer systems. Network communication is the transport of data, voice, video, image, or facsimile (fax) from a single place to one more accomplished by compatibly combining elements of hardware, software program, and media. Core networking—SAIC performs with the highest industry standards to supply a robust and secure core network infrastructure. Computer and network surveillance programs are widespread today, and nearly all World-wide-web site visitors is or could potentially be monitored for clues to illegal activity.
Network communication is the transport of data, voice, video, image, or facsimile (fax) from a single place to one more accomplished by compatibly combining elements of hardware, software program, and media. Core networking—SAIC performs with the highest industry standards to supply a robust and secure core network infrastructure. Computer and network surveillance programs are widespread today, and nearly all World-wide-web site visitors is or could potentially be monitored for clues to illegal activity.